Hi and good weekend to you. I haven’t been writing blog post for 1 week due to Chinese New Year holiday, 1 week off from doing YouTube videos and writing blog post, and spending quality time with my family. This is the first Chinese New Year celebration without visiting friends or other family members. E-angpao has become our replacement of physical AngPao. Seeing how this pandemic pushes technology forward and forcing people from all different generation to use technology, is amazing.
Anyway, this blog post I’m going to be talking about how you as administrator you can exclude certain situation from the Azure ATP detection. Azure ATP stands for Microsoft Defender for Identity. There are few situation you can exclude from Azure ATP detection such as Backup accounts and replication accounts. Take note this is only based on my experience or Microsoft recommendation but is not a MUST to exclude them.
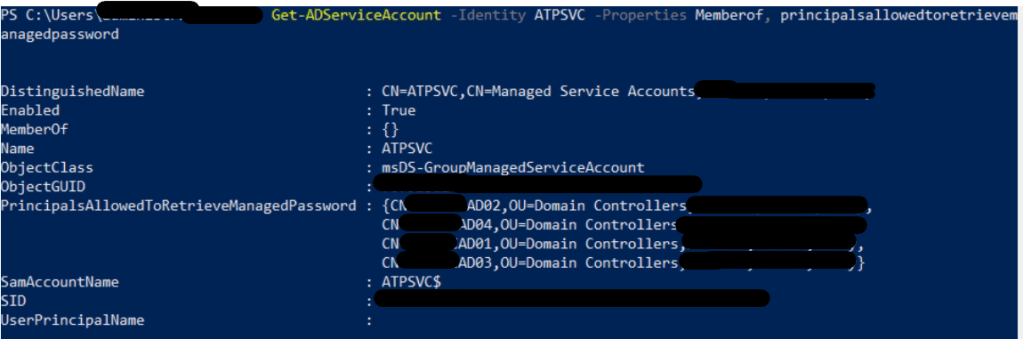
How the alerts works in Azure ATP, is that when ever the account is behaving one of the detection it will notify an alert to the Azure ATP portal and to administrator’s email. So imagine if you have Azure AD Connect in your environment, your Azure AD Connect service account is notifying your administrator every 30 minutes, because the default replication time is every 30 minutes. Annoying right? Once you confirmed that this is the service account used only for replication, here is how you could whitelist it from the Azure ATP detection;
*This is for replication account, for others situation the exclude value may differ, these steps below is mainly to gain understanding how to exclude and where to locate the exclude.
- Login to https://portal.atp.azure.com
- Select Settings
- Under the Detection category
- Select Exclusion
- Locate the detection type and select it
- There you would see 3 sections for your choices on how you want to exclude it
- You can exclude based account name, hostname, IP addresses, subnets and etc..
- Key in the value and remember to save it
- This changes apply immediately
Recommended that you monitor 24 hours. For your information, email notification doesn’t have to be send to same tenant users, it could be external party domain but beware of your auditors.
The portal is a simple user interface, not as confusing as the Security and Protection portal.
References: