Hey guys hope you all are staying indoors and cautions about your health. Today’s blog post is to understand what is gMSA account, how to create them and why does it required for setting up Azure ATP (a.k.a Microsoft Identity Defender ATP).
gMSA stands for group managed service account, below reference that you can refer to understand details about it. You only need to setup a gMSA account for Windows Server version 2012 and above, it is recommended to use gMSA account for you Azure ATP deployment if your Domain controller fall on the versions 2012 and above.
Why gMSA and not usually service account (user object)? It improves the security and automatic password management. It works similar as a managed service account functionality and with extended capabilities, such as password is being managed by your Active Directory and every 30 days a new password is assigned to this service account automatically. If you have mix of legacy domain controllers and newer version of domain controllers, you would need both type of service accounts.
Note:
- Azure ATP directory service connection, doesn’t required a gMSA account, to be a member of domain admin
- If your server doesn’t have the root key created, then run the Add-KdsRootKey command with following parameter “-EffectiveTime“, with value immediately or scheduled.
For this Azure ATP case, all domain controllers with sensor must have managed password permission/right on the gMSA account. Make sure your account has a domain admins right to be able to perform the following setup below;
How to setup a gMSA account?
- On your domain controller
- Open/Launch PowerShell cmdlet
- Type the following command
New-ADServiceAccount -Name <ATP service account name> -DNSHostName <FQDN of 1 of your domain controller> -PrincipalsAllowedToRetrieveManagedPassword <domain controller hostname01$>,<domain controller hostname02$> - Sample of the command
New-ADServiceAccount -Name AzATPSvc -DNSHostName DC01.contoso.com -PrincipalsAllowedToRetrieveManagedPassword DC01$, DC02$ - Retrieve your change result command
Get-ADServiceAccount -Identity AzATPSvc -Properties PrincipalsAllowedToRetrieveManagedPassword - Testing the service account command
Test-ADServiceAccount -Identity AzATPSvc
If your customer is highly concerns about what sort of permission this account is assigned you may run the command below;
- Get-ADServiceAccount -Identity AzATPSvc -Properties MemberOf
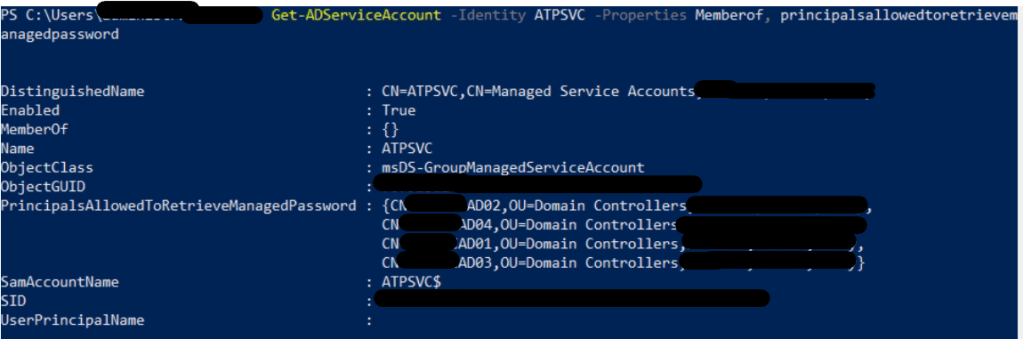
Sample image
References: