Hi everyone, has been months that I’ve not written anything. Hope you guys are having a great time. I had some medical attention needed to attend to and taking the rest that I needed. I’m just here writing about how I started my journey into learning Microsoft Sentinel. I would say it wasn’t piece of cake, and it did take times of tests to run in order to get the results that I wanted. I know that there are a lot of products trying to compete with each other with the concept of SIEM and/or SOAR.

To put them to the comparison is to initiate trial to test out. There is always a hidden purpose of these products, such as prevent and protect based on what’s in their Database. Products that are based on database, to prevent and/or protect tends to require manual action if there are any new virus being found. This doesn’t mean that they aren’t a good product but just depends on your budget, compatible with National Bank Security Policy (Bank Negara), whether you will bite the bullet if anything happens or etc..
I would like to show you some tips on hoping into the technical part of Microsoft Sentinel. I know that for starters you may feel confused on how to start off, you may start off in preparing the correct license (Azure subscription Trial), get the correct permissions to allow you to use the functionality of Microsoft Sentinel, setup your new LA (Log analytics) workspace and you’re good to go.
*Note: Trial license has a MB size limit and expiration date. Please use it wisely or adjust the usage using the limit function.
If you are dealing with license DT (distributor) for getting your Azure license, they tend to worry in providing the permission to the reseller, because afraid that the reseller would done clumsy actions. There are indeed cases had happened. Just make sure prepare your permissions to the DT to assign for you.
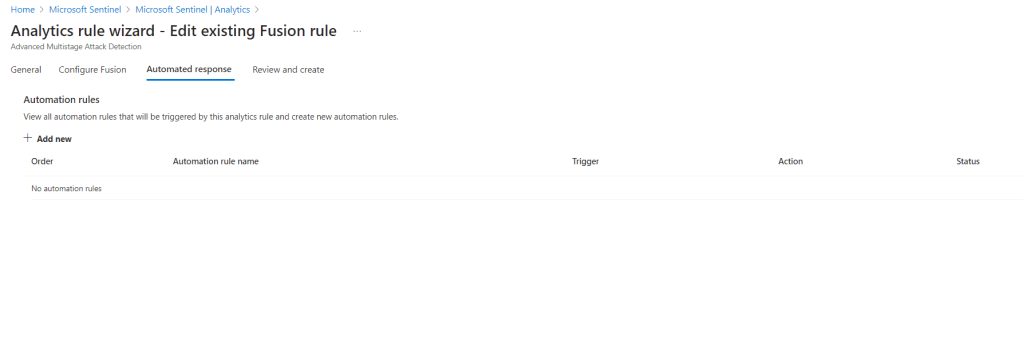
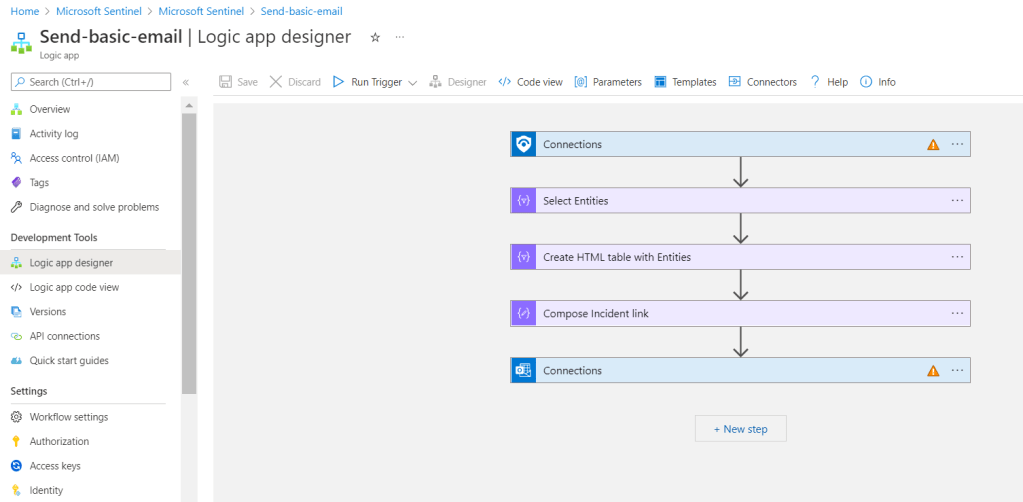
Once you got your basic setup complete, you may go ahead and start your very first script and automation rules and action.
*Note: I have a practice of giving at least 24 to 48 hours for the setup and data transfer (Connector) to the sentinel to be fully propagated.
There are lots of useful scripts that you can find in GitHub but which one would suit this situation? Well, I got my ideas from this link https://github.com/Azure/Azure-Sentinel for more customization scripts would be on your own. There are lots of useful scripts inside there and you can alter it as you like to suit your situations. That’s what I like about Microsoft Sentinel.

If you have any questions about the cost utilization of the Azure subscription, you can ask your license provider and they are kind to help you out.
Referrences: